In this article, we explained how the DMARC policy is evaluated by M365. This article will soon become outdated as, starting from July 13, 2023, Microsoft is rolling out an update to M365 tenants that will impact the handling of incoming emails failing DMARC when their sending domain is protected by a DMARC policy configured in "reject" or "quarantine" mode.
By default, these emails were sent to your users' spam folder.
Starting from August 14, 2023, these emails failing DMARC will be rejected if the sending domain's DMARC policy is set to "reject," and they will be quarantined if the sending domain's DMARC policy is set to "quarantine."
To determine the impact of this change for your organization, you can configure this transport rule:

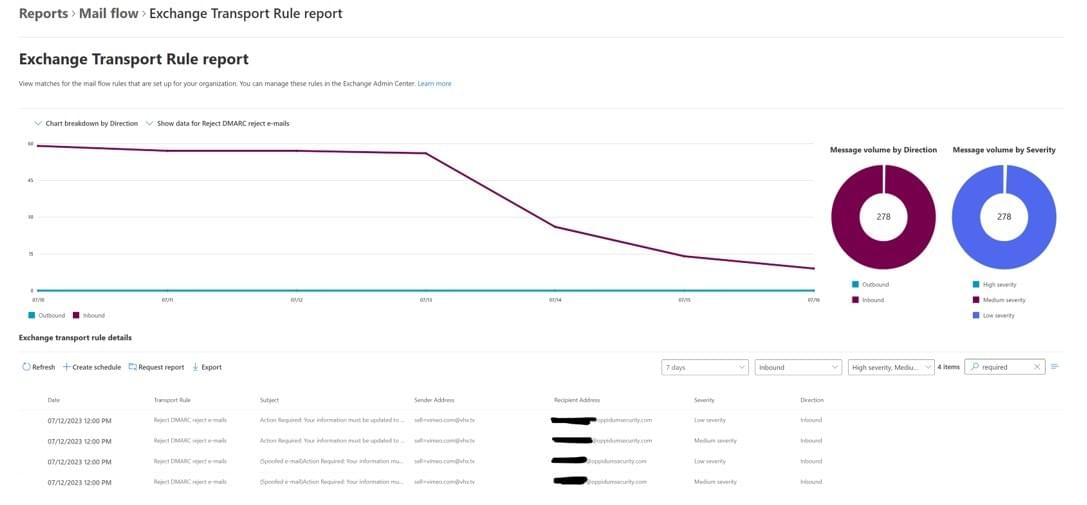
After a few days, you will be able to see the impacted emails here:
If these emails are not already whitelisted in O365 (with SCL=-1 appearing in the email headers), then these emails will be affected by this change.
What to do if important emails fail DMARC? Here are some suggestions:
- Inform the sender, as they may not be aware that their email flows are not DMARC authenticated.
- Whitelist specific senders here: Tenant Allow/Block Lists/Spoofed Senders.
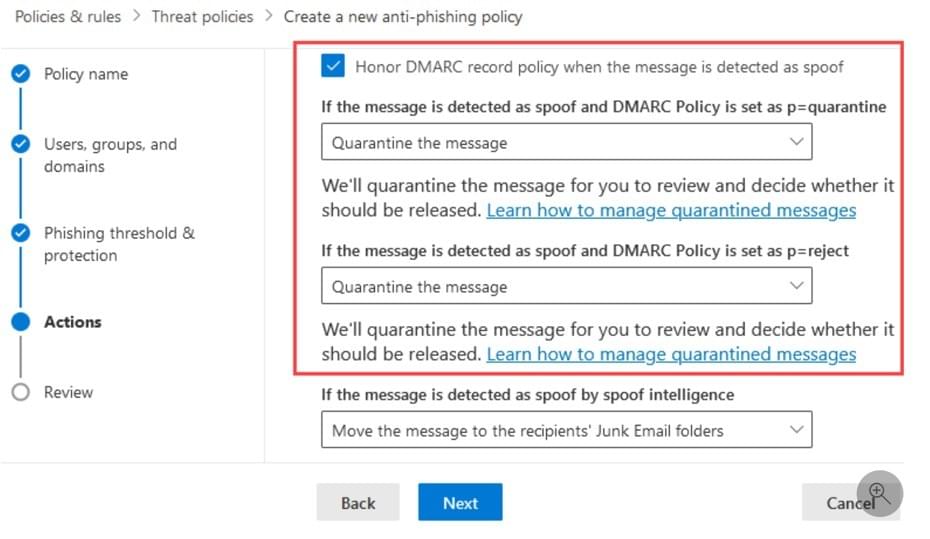
- Consider modifying the default actions when you see these options in your "anti-phishing" filtering policy.