The Outlook "External" warning
Preventing phishing attacks from doing damage is costly for businesses. According to a study by Osterman Research, phishing-related activities consume one-third of the total time of IT and security teams and cost companies anywhere from $2.84 to $85.33 per phishing email.
Most of these attacks come from outside your organization.
To help your users identify emails from outside your organization, it is now possible to enable an option in Microsoft Exchange Online that adds the following warning to external email headers: "External". This warning encourages caution and can reduce the number of users who open phishing emails.
Version Windows Outlook :
Version mobile d’Outlook :
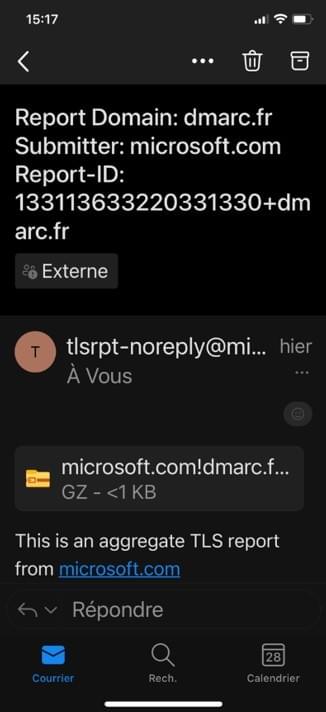
Version web d’Outlook :
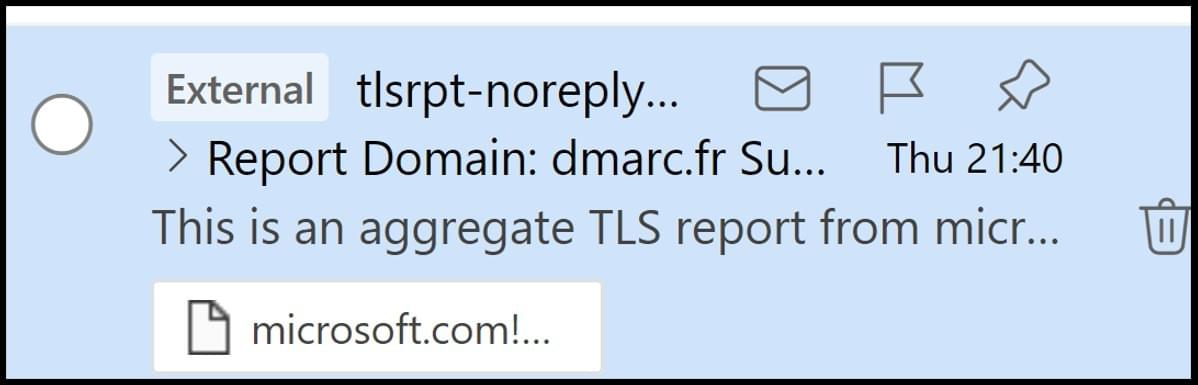
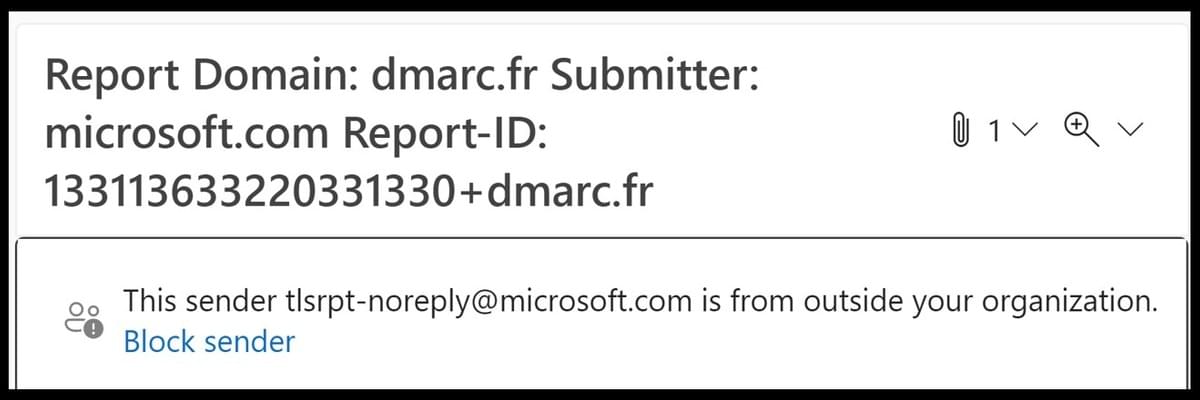
How to set External email warning to Microsoft 365 and Outlook ?
1 Connect to Exchange Online
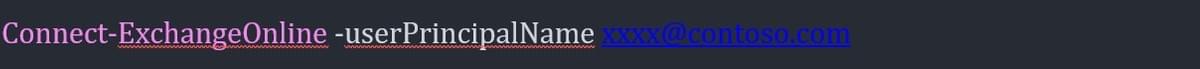
2 Enable external tagging

3 Check for proper activation by typing this command

4 Add or remove domains from the whitelist
You can whitelist domains so that emails sent on behalf of these domains are no longer marked as "external":

You can also remove domains from this list :

You can check the status of this whitelist by typing this command:

Please note that domains already accepted and configured in M365 are already whitelisted.
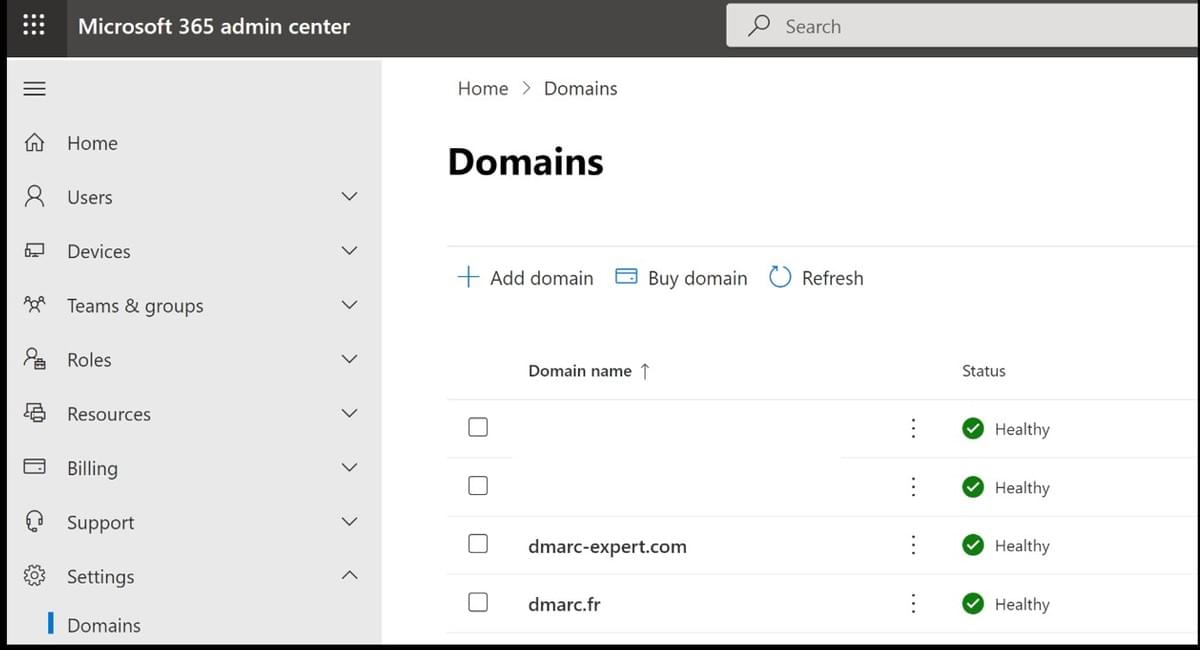
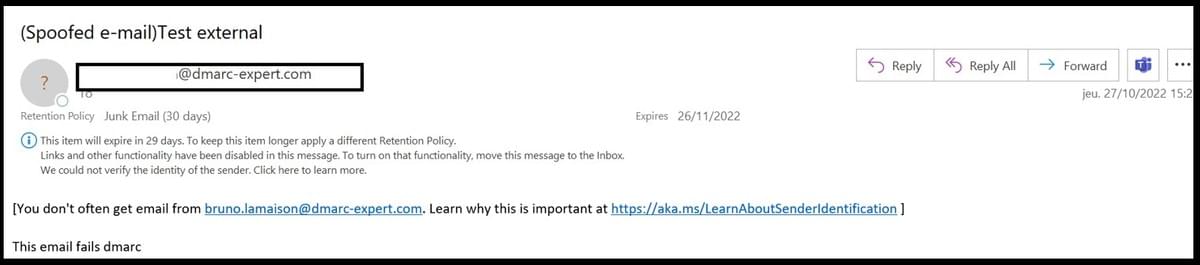
Therefore, an e-mail spoofing your actual e-mail domain name, sent from outside your organization (and thus possibly sent by a hacker), will not be marked as "external" by Outlook, which can pose a risk:
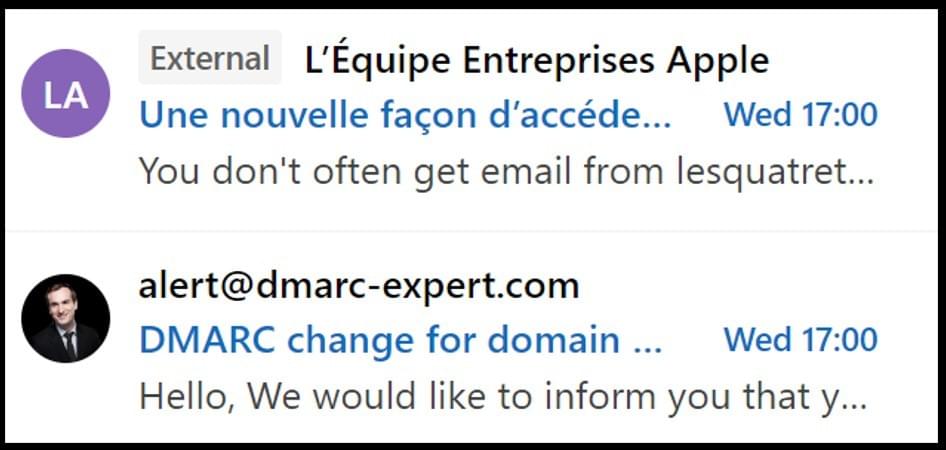
To avoid this situation and prevent fraudsters from misusing your domain, we recommend that you set DMARC to "Quarantine/Reject" mode on your email domain and create a transport rule like this one:

And to add "Spoofed e-mail" in the subject line of e-mails that fail their DMARC compliance checks :
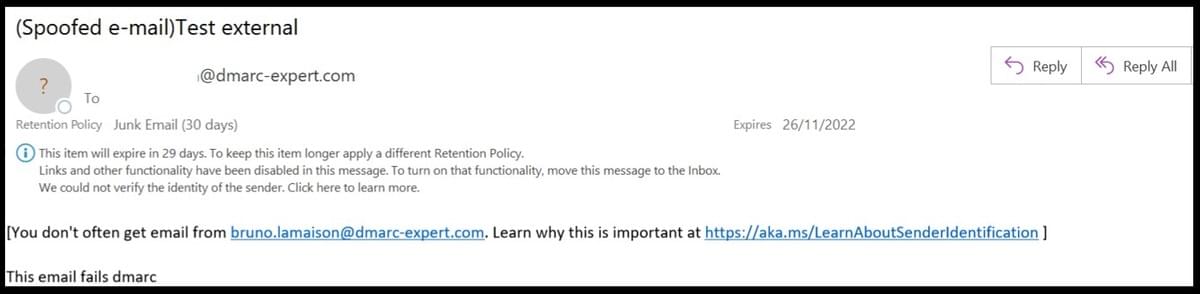
This transport rule will warn your users that the email concerned has not passed DMARC compliance checks and therefore the sender may not be the person specified in the "header from" fields: