Zone.eu analysts recently highlighted an insecure implementation of the "DKIM" email signature protocol: the use of the "l=" tag in the DKIM signature parameters applied to an email (verifiable in the email headers):

This insecure implementation can allow hackers to send emails spoofing the sender's identity while passing the anti-spam tests that verify the authenticity of a message:

Above, the analysts retrieved an email sent by DHL containing the "l=" DKIM tag and were able to forward it with different content while still passing the DKIM/DMARC/BIMI authenticity tests.
How to Protect Against These Attacks if You Are a Sender?
1 Check the headers of the emails you send and ensure that the "l=" tag is not present in the "DKIM-Signature" header.
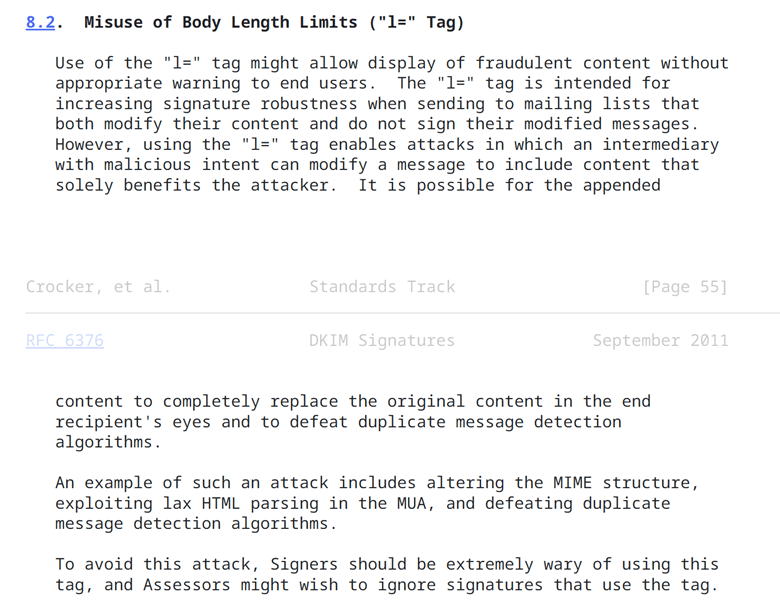
- If it is present, contact the administrator of the sending solution and ask them not to use the "Body Length Limits" option of DKIM when signing emails. Indeed, this option is not recommended by the designers of the DKIM protocol:
- If the sender insists on the necessity of using the "l=" tag, ask if it is possible to protect the "content-type" field in the DKIM signature with the "h=" tag to invalidate the DKIM signature if a hacker modifies the email:
How to Protect Against These Attacks if You Are a Receiver?
As an email recipient, it is important to remain vigilant when you receive an email containing the "l=" DKIM tag.
In Exchange Online, it is possible to configure a transport rule to add a cautionary message for your users when they receive such emails: